Social Engineering is Dead ...
I’m going to start this article off with a story. I was listening to a friend of mine whom we will call Nancy, who is in her sixties, not tech or computer savvy at all, ask a CISO some questions about security the other day. She asked what his job was, and the CISO said, “for better or worse it was to safeguard the data and assets of the company”. My friend then asked if that meant all forms of data? To which the CISO said, yes of course. Again my friend asked, so that means documentation, paperwork, files, because all of that is data, it’s simply stored in a different medium? The CISO thought a moment, and replied, well, I never thought of it that way, but yes I suppose it does.
Nancy then asked about doors, she asked if someone was able to walk into the front door in the middle of the night, walk into an office and steal paperwork, if that would fall under the CISO purview. The CISO replied that indeed it did not, because he had nothing to do with the doors, that wasn’t his job. Nancy came back instantly and said “But you just said, specifically, your job was to safeguard all forms of data? And wouldn’t preventing someone from walking through a door to steal data off of someones desk, literally be your job that you just defined to me?
The CISO slumped a little bit in his chair, looked at the 60 year old women with zero security background and no computer skills, and simply said ..no.. you’re right, I never thought of that either.
I watched this 60 something woman dismantle an “established” CISO on what his own job duties were. She showed an understanding of an executive’s job, better than most executives. She put together what “data” really is (he did not) she put together that cyber security is just simply security, and at the end of the day “Cyber” is quickly becoming a buzzword used to sell products, while security encompasses an entire companies data and assets (in ALL forms). This “ignorant” woman deduced this and put it together in minutes simply by asking a few questions.
I have been working within the “Cyber Warfare” space recently trying to help explain and detail what that means. As I’m not all knowing (although something I like to falsely believe I am), I’ve concentrated on the parts that I do know, which is typically attack methods and cyber espionage. How the “bad actors” attack. What are they doing and how? Research and years of practice always lead back to the same thing, physical access and social engineering.
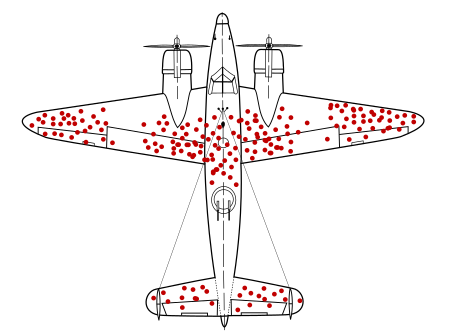
A colleague of mine likes to bring up survivor bias in these instances. As I was a pilot in the USMC, I love the analogy so I’m going to go with it. Security focuses on the things that have been caught, they focus on the “bullet holes” from the plane that returned.
The reality is, the planes that didn’t return, are the ones that you should focus on more. It’s easier for executives to focus on the bullets they see, because companies have made billions creating tools that outline the holes like you see to the right. We should however be focusing on things like the engines, or the propellers, the most important parts of the aircraft. It doesn’t fly without engines or props. Our companies do not exist without people, countries and companies do not function without people or a workforce. Yet our security, both in the government and corporate, ignore the engines, ignores how susceptible people are. They ignore the airframe, the part of the aircraft that gives us structure, the thing that houses the people, or the engines. The human and physical element is constantly overlooked, yet just like the aircraft above… are the most important parts of making sure you fly.
I don’t hate the term “Social Engineering”, I hate that it has become a term that is only synonymous with quarterly phishing exercises. I hate the fact that executives, businesses, even our own government has largely ignored social engineering.
Social engineering, cyber Espionage, is like all of us living on Mt. Saint Helens, there are plenty of signs that point to an eruption. People can’t directly see the signs inside the volcano just the crazy scientists trying to warn them, they constantly say things like “what are the chances”, or “that’s not my job” much to the scientists dismay. The biggest difference, you KNOW when a volcano erupts, when you get hit by a good social engineer, when a threat actor with an advanced skillset attacks you, unless you’re looking for it, and know what to look for, most times you’ll never know. An out of sight, out of mind issue is running rampant in the upper echelons of cyber security decision makers due to pure ignorance.
What if we start using Cyber Espionage and Social Engineering interchangeably? Will executives, companies and governments take the threat more seriously then? Both are extremely complex, with years of study behind them, centuries upon centuries of knowledge associated with both, yet the collective waves its hand as if having KnowBe4 (no offense) fixes it all.
As my 60 year old friend figured out in all of 5 minutes, cyber security is just security. Attacks are sophisticated, attackers are sophisticated, the effort and skillset behind many attacks aren’t just Joe Public off the street trying to settle a score with the City of Seattle. These are professionals, with thousands of years of knowledge behind them. You? Who are you? An executive with zero background in the psychology of how or why any of this works? Do you have a working knowledge of how something simple like your doors in your company SHOULD work and DO work? (those are rarely the same) Are you sure that person texting you is who they say they are? Would you know if they weren’t? Do you have any policies concerning insider threats beyond a “pen test”? Are they enforced? How do you know? Do you know what to look for? Wow, for someone that is in charge of safeguarding the integrity of data and assets, you sure have a lot of holes in your knowledge.
I know you don’t know most, if any of these answers because, once again, we walk into companies like yours every single time, and the scariest part is, it takes such little effort.
Social Engineering is dead, it’s dead because companies have placed it into a box and labeled it “quarterly phishing exercise” and have nearly zero idea just how deadly it IS. It’s dead because employees, service members, agents all across our country lack the proper training on how to spot it, what to do, how to defend. It’s dead because those that actually perform any kind of yearly social engineering are typically financial companies that are relegated to compliance, and simply want the check in box. Call us a few times… ask us for a password and call it good.
Social engineering is dead because decision makers can’t be bothered to be told just how dangerous living on that Volcano can be.
“The greatest trick the Devil ever pulled was convincing the world he didn’t exist.” - Charles Baudelaire