
The Underworld of Ransomware
In today’s digital landscape, stealing data has become easier than pilfering gold, making it a lucrative avenue for criminals. Ransomware, a term many associate merely with malicious software, repr...

In today’s digital landscape, stealing data has become easier than pilfering gold, making it a lucrative avenue for criminals. Ransomware, a term many associate merely with malicious software, repr...


14 BILLION dollars. That’s what MGM Resorts international is worth, 14 BILLION Dollars. Out of that 14 billion dollars, what kind of security program do you think they have? My guess is it’s pretty...

Out of 1000 employees, statistically, 162 of them will allow an attacker into your company. About a week ago someone suggested that there should be certain things that are off limits in phishing. ...

I did some digging today and tried to find the most common reported ways a bad actor gets access to a building or structure. As you can’t gather data on things you aren’t aware that happened (see c...

I’m going to start this article off with a story. I was listening to a friend of mine whom we will call Nancy, who is in her sixties, not tech or computer savvy at all, ask a CISO some questions ab...

Rex Warren passed yesterday April 4th 2023. We are about to forever lose one of the most “OG” and greatest hackers in history. He was always the quiet guy in the back of all the old photo’s, never...

You know, you CAN defend against Social Engineering…. so why would you not want to? It’s only THE #1 way an attacker gets into your system, company and/or building. I’m not sure if its a perceived...
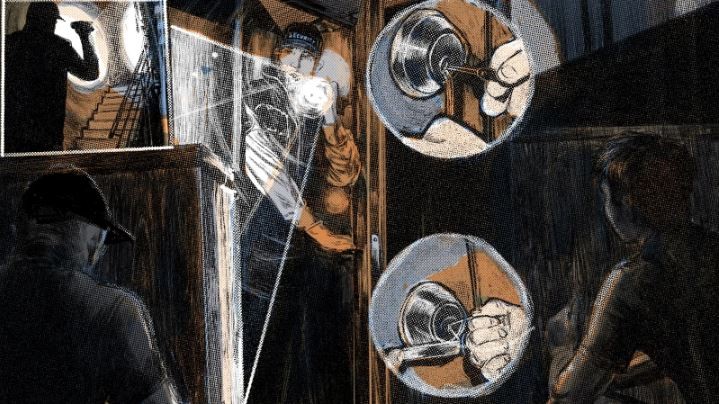
Seriously, what are the odds that we will have someone break into our facility? How likely is it, really, that someone is going to try and social engineer their way into our company? We’ve NEVER ha...

We are all on the fast track to owning and controlling nothing. I first noticed an alarming trend starting to happen back in 2015 when John Deer decided that due to proprietary software, “the vehi...